Security company Symantec has discovered a new malware in the SolarWinds hack. Raindrop was used to install the Cobalt Strike toolkit on a limited number of victims. It is the fourth malware species discovered in the attack.
The malware was discovered by security company Symantec, which wrote a blog post about it . The company discovered a new form of malware used during the SolarWinds hack that took place in December . Presumably Russian state hackers then managed to penetrate the SolarWinds company and infected the network monitoring tool Orion. That way they could penetrate ministries and companies.
Until now, security companies and researchers had found three types of malware that the hackers entered, but now there is one more.
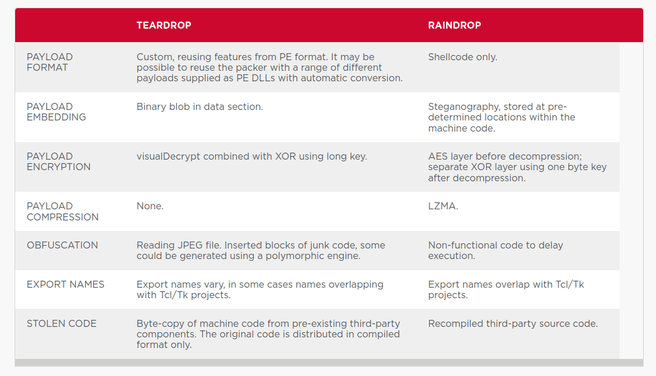
Symantec calls the malware Raindrop. It was only used at a late stage of the hack. The attackers initially used the malware Sunspot to penetrate SolarWinds. Once inside, they infected the Orion software with the Sunburst malware. This was installed at companies via an infected update. Once on those systems, Sunburst was used to deploy the Teardrop malware.
Among other things, Teardrop established a connection to a command-and-control server, where it downloaded Cobalt Strike’s software. This allowed hackers to move through systems in various ways.
According to Symantec, Raindrop is very similar to Teardrop. Raindrop, like Teardrop, is a loader that downloaded the Cobalt Strike payload. Still, Symantec says there are some important differences. In particular, the way Raindrop was installed is unclear.
Raindrop appeared on systems that also contained the Sunburst malware, but does not appear to have been installed via the Sunburst backdoor. The company says it does not yet know how the malware got onto the systems.
The company speculates that Raindrop may have been downloaded via PowerShell. Sunburst was a fileless malware that could execute commands via a shell, among other things, leaving so few traces. However, it is not certain that the malware entered that way. There are also a number of differences between the malware variants, for example in the way in which they make themselves invisible.